CVE-2019-19502
Remote code execution in Image Uploader and Browser for CKEditor 4.1.8 and earlier.

CVE
Vendor and Product
Image Uploader and Browser for CKEditor
Versions Affected
4.1.8 and earlier.
Risk and Severity Rating
CVSS Base Score: 8.8 (High)
CVSS Vector String: CVSS:3.0/AV:N/AC:L/PR:L/UI:N/S:U/C:H/I:H/A:H
Vulnerability
Image Uploader and Browser for CKEditor 4.1.8 and earlier suffers from code injection vulnerability via PHP string interpolation. This allows attackers to execute arbitrary PHP code which can lead to remote code execution.
Authentication as a user is required to exploit this vulnerability. However, in some cases, authentication is not required as protection can be disabled by developer/administrator.
Technical Details
This plugin stores settings, such as upload path, into pluginconfig.php. It already sanitized the path using FILTER_SANITIZE_STRING. You can view the source code here.
if(isset($_POST["newpath"])){
$newpath = filter_input(INPUT_POST, 'newpath', FILTER_SANITIZE_STRING);
$root = $_SERVER['DOCUMENT_ROOT'];
$data = '
$useruploadfolder = "'.$newpath.'";
$useruploadpath = $usersiteroot."$useruploadfolder/";
$foldershistory[] = "'.$newpath.'";
'.PHP_EOL;
$fp = fopen( __DIR__. '/pluginconfig.php', 'a');
fwrite($fp, $data);
}However, the upload path is stored into a PHP variable named $useruploadfolder and appended into $folderhistory with double quotes. In PHP, double-quoted strings will be parsed. For example:
<?php
$name = "Visat";
echo "Hi my name is $name";
?>Running above code in PHP will output Hi my name is Visat. Moreover, PHP has a feature named complex (curly) syntax. Basically it allows more complex expressions such as accessing object property.
<?php
$name = "Visat";
echo "Hi my name is {$name}";
echo "Hi my name is ${name}"; // variation
class Person { public $name = "Visat" }
$person = new Person();
echo "Hi my name is {$person->name}";
?>Another interesting thing is this curly syntax can be used to call a function.
<?php
$func = "phpinfo";
$info = "{$func()}"; // this will output PHP info
?>This feature can be abused to achieve remote code execution in this plugin. If a user saves the upload path using curly syntax which calls a function inside the syntax, the function will be called.
Proof of Concept
Login to Image Uploader and Browser for CKEditor 4.8.1 and earlier, then set the upload path to ${phpinfo()} on the settings page. Refresh the page and PHP info will be printed.
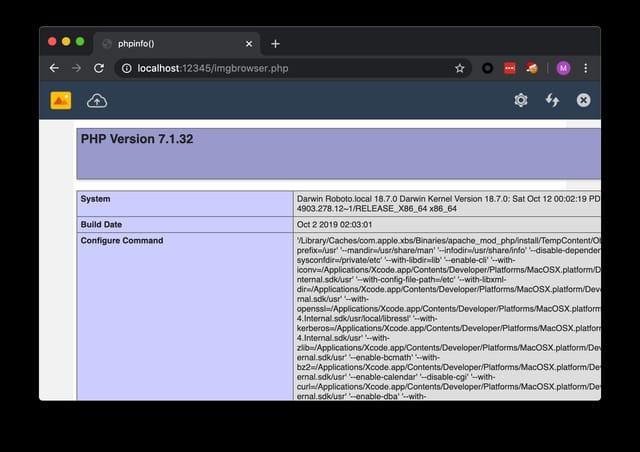
phpinfo().The phpinfo function then can be replaced by other PHP functions to achieve remote code execution on the server.
Solution
Upgrade to Image Uploader and Browser for CKEditor 4.1.9 or later here.
References
Timeline
- 14/08/2019 – Reported vulnerability to author.
- 19/08/2019 – Author acknowledged the vulnerability.
- 30/11/2019 – Proposed a patch via pull request and got merged.
- 31/11/2019 – Author released version 4.1.9.
- 02/12/2019 – CVE-2019-19502 was assigned to this vulnerability.
- 22/12/2019 – Full disclosure.
